If you’d like to know about all things CSA STAR, you’ve come to the right place. In this blog, created by the compliance experts at ControlCase, we’re going to ask and address the following questions and topics:
• What is the Cloud Security Alliance?
• Why the STAR Program
• CSA STAR Levels of Assessment
• CSA STAR Cloud Controls Matrix and Domains
• The Cloud Security Alliance STAR Certification Program
• Cloud Security Alliance Questionnaire CAIQ
• The STAR Registry
What is the Cloud Security Alliance?
Why the Cloud Security Alliance STAR Certification Program?
The CSA established the STAR program as a solution for cybersecurity compliance throughout the widespread adoption of cloud services. STAR stands for Security, Transparency, Assurance, and Risk.The overall goal of the CSA STAR Program is to bring in the key principles of the Cloud Controls Matrix while providing total transparency and helping clients adhere to specific requirements. This is accomplished through the CSA STAR Program…
…providing the tools to evaluate cloud services.
…establishing a way for providers to prove the compliance and security measures their company takes.
…creating a registry to bring together all information.
The STAR Program assists enterprises, or anyone in the cloud computing market, in evaluating the risk to an organization and implementing controls based upon identified risks.
Specifically, the STAR Program offers assurance against a very heterogenous (with common needs and issues) cloud computing market by supporting organizations in effectively and efficiently addressing these dedicated areas:
• Defining trust in the cloud
• Fostering accountability
• Evaluating risk.
• Measuring assurance
• Simplifying compliance and procurement.
CSA STAR Levels of Assessment
There are multiple levels of assessment when it comes to CSA STAR.
CSA STAR Levels 1 and 2 cover Self-Assessments and Third Party Audits, as seen in the following table:
STAR Level 3 is Continuous Auditing, as seen in the following graphic: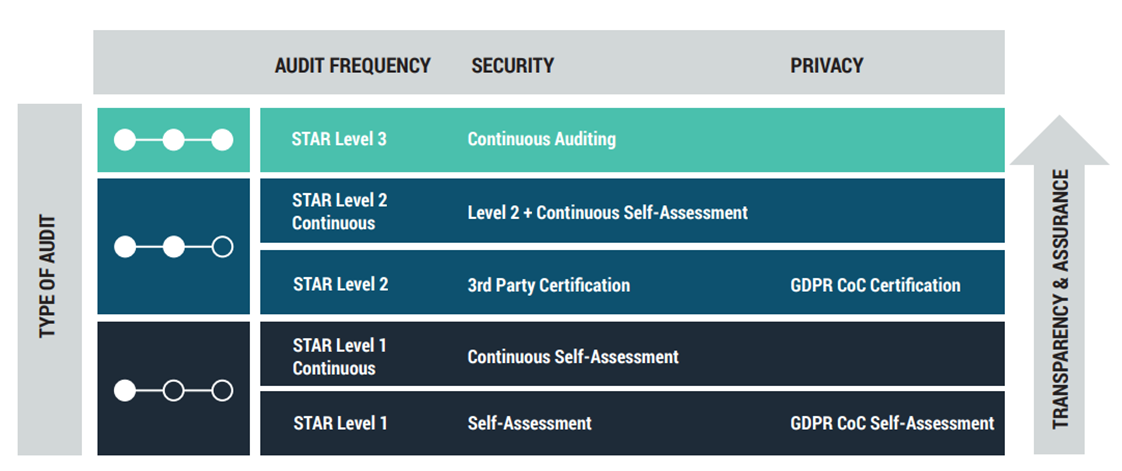
CSA STAR Cloud Controls Matrix and Domains
The Cloud Security Alliance Cloud Controls Matrix (CSA CCM) is a cybersecurity control framework for cloud computing, as mentioned on the CSA website. The Cloud Controls Matrix structure is based around the ISO 27001 structure with a specific focus on cloud computing.
197 control objectives make up the CSA CCM. The control objectives are structured in the 17 Cloud Security Alliance domains, with the goal of thoroughly encompassing all aspects of cloud computing.
Following are the 17 CSA Domains:
• Application & Interface Security
• Audit and Assurance
• Business Continuity Mgmt & Op Resilience
• Change Control & Configuration Management
• Cryptography, Encryption, and Key Management
• Datacenter Security
• Data Security & Privacy
• Governance, Risk Management, and Compliance
• Human Resources Security
• Identity & Access Management
• Interoperability & Portability
• Infrastructure & Virtualization Security
• Logging and Monitoring
• Security Incident Management, E-Discovery, & Cloud Forensics
• Supply Chain Management, Transparency, & Accountability
• Threat & Vulnerability Management
• Universal EndPoint Management
Cloud Security Alliance Questionnaire CAIQ v4
The Consensus Assessment Initiative Questionnaire (CAIQ) consists of yes or no questions for cloud consumers and auditors to ask a cloud provider to assess their compliance against the Cloud Controls Matrix. The CAIQ helps customers determine the level of security maintenance in prospective providers. The CAIQ results are submitted to the STAR Registry.
STAR Registry
In the spirit of transparency, the STAR Registry hosts a public repository for cloud market assessments to perform risk-based cloud services. A requirement of the CSA STAR Program is that organizations must publish their results on the STAR Registry, making the information freely accessible by anyone. The establishment of a public registry makes the CSA STAR unlike other frameworks.
