As the landscape of cyber threats continues to evolve, it becomes increasingly critical for businesses that handle cardholder data to proactively implement robust security measures to safeguard sensitive information. In this regard, ControlCase offers expert assistance and support in establishing and maintaining comprehensive security protocols to protect cardholder data from potential risks and breaches.
The deadline for meeting the final 51 PCI DSS v4.0 “best practices” requirements is fast approaching as we near the end of 2024. Does your company need to be compliant? After March 31, 2025, all certifications will be required to adhere to the updated standards. New requirements are currently best practices but will be mandatory in March. ControlCase can help! Make sure everything is in place before the deadline.
PCI DSS v4.0
PCI Data Security Standard (PCI DSS) is a global standard that establishes baseline technical and operational requirements to safeguard account data. The latest iteration of the standard, PCI DSS v4.0, is now accessible.
PCI DSS v4.0 New Requirements
Requirement 1: Install and maintain network security controls
Network security controls (NSCs), including firewalls and other network security technologies, serve as enforcement points for network policies. They are responsible for regulating network traffic between various logical or physical network segments (or subnets) based on predefined rules or policies. While this function has traditionally been fulfilled by physical firewalls, it is now also achievable through virtual devices, cloud access controls, virtualization/container systems, and other software-defined networking technology.
Requirement 2: Apply secure configurations to all system components
Malicious individuals, whether internal or external to an organization, often exploit default passwords and other vendor settings to compromise systems. These well-known passwords and settings can be easily obtained from public information.
Implementing secure configurations for system components is crucial for reducing the vulnerabilities that attackers can exploit to compromise systems. This involves actions such as changing default passwords, eliminating unnecessary software, functions, and accounts, and disabling or removing redundant services. These measures collectively contribute to minimizing the potential attack surface and enhancing overall system security.
Requirement 3: Protect stored account data*
It is important to refrain from storing payment account data unless it is absolutely necessary for the business’s operations. Under no circumstances should sensitive authentication data be retained after authorization has been granted. If your organization maintains Primary Account Numbers (PAN), it is imperative to ensure that they are rendered unreadable. Additionally, if your company retains sensitive authentication data before the authorization process is completed, it is crucial to implement robust protection measures for this data as well.
Requirement 4: Protect cardholder data with strong cryptography during transmission over open, public networks
In order to prevent unauthorized access, it is important to encrypt primary account numbers (PANs) when they are being transmitted over networks that can be easily accessed by malicious individuals, including untrusted and public networks. Malicious individuals often target misconfigured wireless networks and vulnerabilities in outdated encryption and authentication protocols in order to gain privileged access to cardholder data environments (CDE). To protect PAN transmissions, the data can be encrypted before it is transmitted, or the session over which the data is transmitted can be encrypted, or both.
Requirement 5: Protect all systems and networks from malicious software
Malicious software, also known as malware, refers to software or firmware created to infiltrate or harm a computer system without the owner’s knowledge or consent. Its goal is to compromise the confidentiality, integrity, or availability of the owner’s data, applications, or operating system. Examples of malware include viruses, worms, Trojans, spyware, ransomware, keyloggers, rootkits, malicious code, scripts, and links. Malware can enter a network through various business-approved activities, such as employee email (e.g., via phishing) and the use of the internet, mobile computers, and storage devices. This can lead to the exploitation of system vulnerabilities.
Requirement 6: Develop and maintain secure systems and software
Security vulnerabilities in systems and applications can allow criminals to access payment data. Many of these vulnerabilities can be fixed by installing security patches provided by the vendor. These patches quickly repair specific areas of the code. To prevent exploitation, it’s important to have the latest critical security patches installed on all system components. Additionally, patches should be applied to less critical systems within a reasonable timeframe, based on a formal risk analysis. Applications should be developed using secure coding practices, and any changes to systems in the cardholder data environment must follow change control procedures.
Requirement 7: Restrict access to cardholder data by business need-to-know
Unauthorized individuals could potentially access important data or systems due to ineffective access control rules and definitions. To prevent this, it’s crucial to have systems and processes in place to restrict access based on necessity and job responsibilities. “Need to know” means granting access to the minimum amount of data required to perform a job, while “least privileges” means providing only the essential level of privileges needed for a job.
Requirement 8: Identify users and authenticate access to system components*
To maintain security, it’s important to assign a unique ID to each person who has access to ensure that actions taken on critical data and systems can be traced back to authorized users. These requirements apply to all accounts, including point-of-sale accounts, those with administrative capabilities, and all accounts used to view or access payment account data or systems. It’s important to note that these requirements do not apply to accounts used by consumers (cardholders) unless otherwise stated.
Requirement 9: Restrict physical access to cardholder data
Access to cardholder data or systems storing, processing, or transmitting cardholder data must be restricted to prevent unauthorized access or removal of data systems or hardcopies.
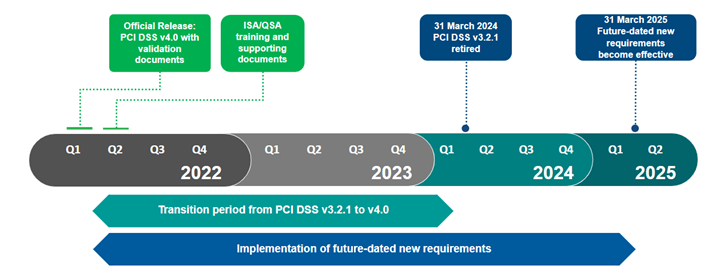
Implementation Timeline
Below is the implementation timeline for PCI DSS v4.0.
The PCI DSS v4.0 New Requirements Assessment Will Include:
- Initial Consultation and Scope Review
- Validation of new controls and relevant Documentation Review
- Comprehensive Gap Identification
- Designing an Actionable Roadmap
- Access to ControlCase’s groundbreaking Compliance Hub™ platform
PCI DSS v4.0 Current Best Practices*
Requirements 3 and 8 will be considered best practices until 2025. ControlCase’s offering involves reviewing and evaluating the customer’s current position in relation to the new requirements. The assessment will specifically concentrate on requirements 3 and 8. The objective is to analyze the customer’s current status regarding requirements 3 and 8 to guarantee timely compliance with these mandatory standards by March 2025.
ControlCase’s PCI DSS v4.0 Offerings
ControlCase is the leading provider of cybersecurity services and IT compliance audits. Our offerings include PCI DSS v4.0. We are known for leveraging cutting-edge technology and employing highly skilled personnel to deliver exceptional results.
ControlCase’s Compliance Hub™ enables organizations to achieve compliance with multiple standards simultaneously. The platform streamlines the process by facilitating technology-driven information gathering. It also offers a real-time dashboard that visualizes compliance efforts, allowing teams to communicate progress and needs effectively.
Customers who finish the PCI DSS v4.0 New Requirements Assessment and proceed with ControlCase’s comprehensive PCI DSS Assessment at the gold standard level will be eligible for substantially discounted pricing.
Secure your spot now and make sure that your company is fully compliant with the March 31 PCI deadline for DSS v4.0 requirements.
To learn more, connect with us on LinkedIn, or feel free to reach out to our team of experts at contact@controlcase.com.
