Why HITRUSTTM is Essential for Security and Compliance Assurance
Protecting sensitive data and maintaining privacy are now core business requirements. As information security regulations grow more rigorous and stakeholder expectations rise, organizations that handle sensitive information must meet higher compliance standards with confidence. HITRUSTTM has emerged as a leading framework to help organizations achieve and demonstrate that level of security assurance.
What Is HITRUSTTM and Why Organizations Adopt It
Originally created for the healthcare industry, HITRUSTTM offers a certifiable framework that ensures organizations’ security and privacy practices align with various regulations. Over time, HITRUSTTM has evolved into a flexible, threat-adaptive framework now used across industries. Although adopting HITRUSTTM can be demanding, it helps companies meet their compliance goals and demonstrates a strong commitment to data protection.
Why Organizations Choose ControlCase for HITRUSTTM
ControlCase is a global leader in certification and cybersecurity services, making challenging certification processes, like HITRUSTTM, a lot simpler. With over a decade of experience as a HITRUSTTM Authorized External Assessor, they know the ins and outs of HITRUSTTM assessments. As a key member of the HITRUSTTM Assessor Council, they help shape industry best practices, which means they are always up to date on the latest security and privacy standards. Their hands-on, expert approach ensures organizations can achieve certification with confidence and ease.
Understanding the HITRUSTTM Assessment Approach
Achieving HITRUSTTM certification is not a one-size-fits-all process. Every organization starts from a different level of maturity, which is why HITRUSTTM offers multiple assessment types. Before diving into the key elements of a successful HITRUSTTM implementation, it is important to understand these assessment stages and why they matter.
HITRUSTTM Assessment Types: Choosing the Right Path
- HITRUSTTM e1 Validated Assessment
The e1 (Essential 1 year) assessment is designed for organizations with lower risk profiles or those early in their compliance journey. It focuses on a foundational set of cybersecurity controls and provides a practical starting point for establishing security hygiene. - HITRUSTTM i1 Validated Assessment
The i1 (Implemented 1 year) assessment is suited for organizations with moderate risk exposure. It evaluates whether a defined set of security controls are implemented and operating effectively, offering a streamlined validation option without the full complexity of an r2 assessment. - HITRUSTTM r2 Assessment
The r2 (Risk-based 2 year) assessment is the most comprehensive HITRUSTTM assessment and is typically required for organizations operating in high-risk or highly regulated environments. It assesses the design, implementation, and operational effectiveness of controls across a broader scope.
Regardless of whether an organization pursues an e1, i1, or r2 assessment, certain core elements play a critical role in determining success.
Core Elements of a Successful HITRUSTTM Journey
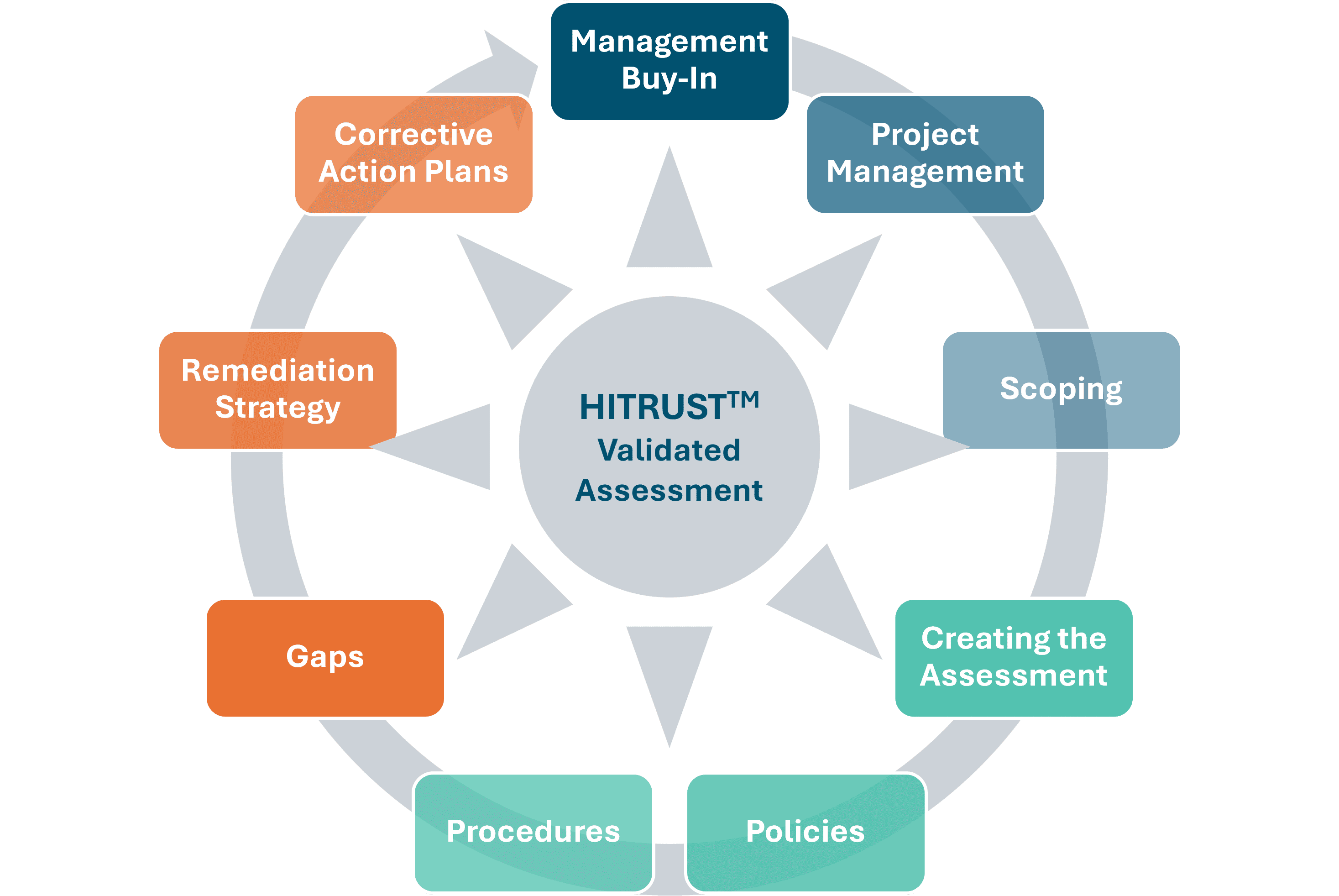
1. Management Buy-in
For any compliance framework to be effectively implemented, management buy-in is essential. Securing support from senior leadership provides the necessary resources and ensures that HITRUSTTM initiatives align with the organization’s overall strategy. Management must understand the long-term benefits of HITRUSTTM certification, including building customer trust and avoiding costly regulatory penalties.
2. Project Management
Getting HITRUSTTM certified might seem overwhelming, but good project management makes all the difference. It is all about planning, organizing tasks, and keeping an eye on resources to stay on track with the HITRUSTTM assessment. Breaking things down and staying organized can make the entire process much smoother.
3. Scoping
Proper scoping is essential for defining the boundaries and parameters of the HITRUSTTM assessment. This includes identifying all systems, processes, data flows, and organizational units that are within the scope of the assessment. A well-defined scope ensures that the assessment is comprehensive, accurate, and aligned with the organization’s unique security requirements.
4. Creating the Assessment
To create a HITRUSTTM assessment, the assessed organization needs to understand their organization’s goals and scope. This means figuring out what’s required based on general, organizational, technical, and compliance factors. It is about tailoring the assessment to fit the assessed organization’s unique business needs.
5. Applicability
Understanding the applicability of HITRUSTTM requirements to the organization’s specific environment is essential for effective compliance management. This involves mapping HITRUSTTM controls to the organization’s systems and platforms to ensure that all relevant security controls are implemented and maintained. By aligning HITRUSTTM requirements with the organization’s unique operational context, organizations can ensure that their compliance efforts are tailored, relevant, and impactful in addressing their specific security needs.
6. Policies
Developing and implementing robust policies that align with HITRUSTTM requirements is a foundational element of compliance management. Policies serve as the framework for security governance, outlining the organization’s expectations and responsibilities related to information security. Well-crafted policies address key security domains, such as data protection, access control, incident response, and risk management, and provide clear guidance on complying with HITRUSTTM standards.
7. Procedures
Procedures translate policies into action. While policies explain “what” needs to be done, procedures detail “how” it is done. Effective implementation of HITRUSTTM involves ensuring that all procedures are aligned with policies and can be demonstrated during the assessment process.
8. Gaps
Gap analysis is a critical part of the HITRUSTTM process. This step identifies the differences between the assessed organization’s current security posture and HITRUSTTM’s requirements. Pinpointing gaps early allows organizations to prioritize efforts and focus on the areas needing the most improvement.
9. Remediation Strategy
After identifying any gaps, the next step is to create a remediation strategy to fix them. This strategy shows how the organization will close the gaps in their security controls to meet HITRUSTTM standards. A thorough remediation strategy is essential for refining the security posture and staying resilient against cyber threats.
10. Corrective Action Plans
If any issues or non-compliances are identified during the assessment, a corrective action plan (CAP) must be developed. Corrective action plans (CAP) outline the specific actions, responsible parties, and timelines required to remediate the identified non-compliances.
ControlCase’s Approach to HITRUSTTM Assessments
At ControlCase, we start by collaborating with the assessed organization to determine the scope of the HITRUSTTM assessment. This involves identifying the systems and platforms they have in place and figuring out the key focus areas. Once we establish that, we will perform a gap analysis to evaluate the assessed organization’s existing controls against HITRUSTTM requirements. This process helps us highlight areas that need improvement and ensures we concentrate on what matters the most.
Following the gap analysis, we work with the assessed organization’s team to prioritize which gaps to tackle first, zeroing in on the high-impact areas that are essential for certification. We then create a straightforward roadmap that outlines the specific actions needed to achieve compliance, ensuring everything aligns with HITRUSTTM standards. By setting clear milestones, we help the assessed organization’s team manage each phase without feeling overwhelmed.
We also assist in aligning the assessed organization’s internal policies and procedures with the HITRUSTTM framework. This involves reviewing their current documentation to make sure it meets HITRUSTTM requirements, which is vital for demonstrating compliance during the assessment.
Throughout this journey, our team provides hands-on guidance and works closely with the assessed organization’s internal teams to address identified gaps and strengthen their security posture. Once we are confident in the assessed organization’s readiness, we transition seamlessly into the formal HITRUSTTM audit phase, and the ControlCase Audit team oversees validation activities and quality checks to ensure a smooth and well-governed certification process. This structured, end-to-end approach helps organizations move forward with confidence, knowing each step is aligned with HITRUSTTM expectations.
At ControlCase, our proven HITRUSTTM methodology adapts to your certification type while maintaining a consistent, efficient approach, helping you put the right foot forward from day one and confidently achieve certification.
To learn more about how ControlCase can help you with your HITRUSTTM needs, contact us.
