
ControlCase Advisory on the Shellshock Vulnerability
This is a security advisory on the “Shellshock” vulnerability.
What is Shellshock
Bourne Again Shell (bash) is a widely used shell on *NIX systems. It contains flaw that allows attacker to provide specially-crafted environment variables containing arbitrary commands that can be executed on vulnerable systems under certain conditions. So far, HTTP requests to CGI scripts have been identified as the major attack vector.The impact of exploitation of this vulnerability is as big as “Heartbleed” because of wide use of bash.
With access to bash even from the web servers using CGI, there are possibilities to create denial of service (DOS) on servers, distributed DOS (DDOS), steal data from servers and complete compromise of server/network.
Current bash versions use an environment variable named by the function name, and a function definition starting with “() {” in the variable value to propagate function definitions through the environment. The vulnerability occurs because bash does not stop after processing the function definition. it continues to parse and execute shell commands following the function definition. For example, an environment variable setting of
![]()
will execute ping command when the environment is imported into the bash process.
GNU Bash versions till 4.3 are all known to be vulnerable.
How ControlCase CaaS Customers can request test for Shellshock
ControlCase can perform Shellshock test for your infrastructure and provide you the results. ControlCase Compliance as a Service (CAAS) customer can request “Shellshock Test” by using following steps.
-
- Login to IT GRC portal
- Click “External PT Scan Form” link on the dashboard
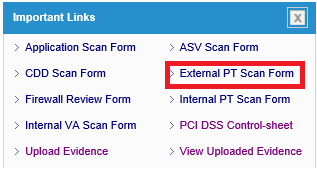
-
- Fill the External Network Penetration Test form with all the details and mention “Shellshock” before filling public IP addresses against #6
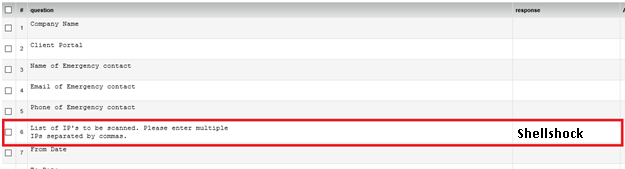
-
- Once form is filled completely, click Notify button on top right corner
![]()
How to test if you are vulnerable
You can test your shell if it is vulnerable using following method.
![]()
Upon running the above command, an affected version of bash will output “BINGO”.
If it is not vulnerable, the same test will return the following result.
![]()
The above test is to only determine if you are running vulnerable version of bash.
How to fix
There is no direct patch available at the time of writing this advisory. The original fix for this issue was incorrect; CVE-2014-7169 has been assigned to cover the vulnerability that is still present after the incorrect fix.
Workarounds
- If possible, you can disable access to cgi script directories available through a web interface because in a lot of cases, it may be enabled but not actually used.
- If cgi access is needed; if possible, restrict the usage to a list of known IPs
- Setup rules in your logging and monitoring solution to identify access to cgi directories and raise alerts for such access
References
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7169