
GHOST Vulnerability Advisory
This is a security advisory on the “GHOST Vulnerability (CVE-2015-0235).”
About the Vulnerability
The GHOST vulnerability is a serious weakness in the Linux “glibc library”. It allows attackers to remotely take complete control of the victim system.
GHOST is a ‘buffer overflow’ vulnerability affecting the gethostbyname() and gethostbyname2() function calls in the glibc library. This vulnerability allows a remote attacker that is able to make an application call to either of these functions to execute arbitrary code with the permissions of the user running the application.
The first vulnerable version of the GNU C Library affected by this vulnerability is glibc-2.2, released on November 10, 2000. The vulnerability was fixed on May 21, 2013 (between the releases of glibc-2.17 and glibc-2.18). Unfortunately, it was not recognized as a security threat; as a result, most stable and long-term-support distributions were left exposed.
Affected Distributions
- RHEL (Red Hat Enterprise Linux) version 5.x, 6.x and 7.x
- CentOS Linux version 5.x, 6.x & 7.x
- Ubuntu Linux version 10.04, 12.04 LTS
- Debian Linux version 7.x
- Linux Mint version 13.0
- Fedora Linux version 19 or older
- SUSE Linux Enterprise 11 and older (also OpenSuse Linux 11 or older versions).
- SUSE Linux Enterprise Software Development Kit 11 SP3
- SUSE Linux Enterprise Server 11 SP3 for VMware
- SUSE Linux Enterprise Server 11 SP3
- SUSE Linux Enterprise Server 11 SP2 LTSS
- SUSE Linux Enterprise Server 11 SP1 LTSS
- SUSE Linux Enterprise Server 10 SP4 LTSS
- SUSE Linux Enterprise Desktop 11 SP3
- Arch Linux glibc version <= 2.18-1
How ControlCase CaaS Customers can request a test for GHOST Vulnerability
ControlCase Compliance as a Service (CaaS) customers can request “GHOST Vulnerability Scan” by using the following steps:
-
- Login to IT GRC portal
- Click “Internal VA Scan Form” link on the dashboard
-
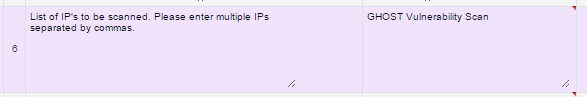
- Fill the Internal VA Scan form with all the details and mention “GHOST Vulnerability Scan” before filling Internal IP addresses against #6
-
- Once form is filled completely, click Notify button on top right corner
![]()
Pre-Requisites for GHOST Vulnerability Scan
Following are the pre-requisites to perform the successful GHOST vulnerability scan:
- SSH access to the targeted scope for ControlCase Appliance IP Address
- Root or root equivalent credentials to perform the scan (information shall be shared via ControlCase Secure Portal)
How to test if you are vulnerable
The easiest way to check vulnerability and/or confirm remediation is to run the following command to verify that you are running an updated version of glibc (v2.20) $ ldd -version
How to fix
Ubuntu: https://launchpad.net/ubuntu/+source/eglibc
CentOS: http://lists.centos.org/pipermail/centos-announce/2015-January/020906.html
OpenSUSE: http://lists.opensuse.org/opensuse-updates/2015-01/msg00085.html
References
http://www.cyberciti.biz/faq/cve-2015-0235-patch-ghost-on-debian-ubuntu-fedora-centos-rhel-linux/